top of page


The PAM Commandments
In a previous blog , I discussed the basics of IAM (Identity Access Management), which encompasses IGA (Identity Governance and...

Eva Vetter
Jul 17, 20252 min read


Embrace the Daily Dare: Conquer Your Fears!
I am deeply inspired by stories of unwavering determination, especially when they require immense patience to achieve the desired...

Eva Vetter
Jul 9, 20251 min read


Identity + Legacy Data
Excited to share a thought-provoking blog by Justin Gallardo at ConductorOne that delves into the realms of Identity and data, two areas...

Eva Vetter
Jul 4, 20251 min read


Thinking Outside the Box as a Job Seeker
As a helpful tip for fellow job seekers, I want to share a resource that has been invaluable in my job search beyond platforms like...

Eva Vetter
Jul 4, 20251 min read

Hello, I Am Your AI Assistant
I find myself reflecting on the common trait of being highly critical of one's own work, a sentiment shared by many. Whether it pertains...

Eva Vetter
Jul 4, 20251 min read

The Foundations of IAM
Previously I discussed the essential pre-onboarding questions for a new IdP (Identity Provider) vendor. In that conversation, I mentioned...

Eva Vetter
Jul 4, 20251 min read


Saviynt Offers Inclusive Training
When you're passionate about a subject, learning more about it doesn't feel like a chore. For me, Product Management and IAM (Identity...

Eva Vetter
Jul 4, 20251 min read


Did You Attend Identiverse?
For those that attended Identiverse I would be delighted if you could share any summaries of the events you attended either in a post or...

Eva Vetter
Jul 4, 20251 min read


Job Hunting and Identity Verification
In the realm of job hunting, the importance of verification cannot be overstated. Ensuring the legitimacy of both the employer and the...

Eva Vetter
Jul 4, 20251 min read


User Access: Deprovisioning Stage
When we discuss Product Management or User Access, the focus often gravitates towards the initial launch or provisioning phase. Yet,...

Eva Vetter
Jul 4, 20251 min read


IAM is too Niche?!
My Tangy Take: I was criticized recently due to my love of Identity as I was told it was too narrow of a field to focus on. I would...

Eva Vetter
Jul 4, 20251 min read


RBAC + AI?
In 2017, I started troubleshooting RBAC (Role-Based Access Control) for enterprise customers, grappling with the intricacies of roles,...

Eva Vetter
Jul 3, 20251 min read


PoLP (Principle of Least Privilege)
Looking back to my early days as an apprentice in the Information Technology realm, the significance of IAM (Identity Access Management)...

Eva Vetter
Jul 3, 20251 min read


SAML SSO 201
Previously I had spoke about the basics of a certain flavor of SSO (Single Sign On) which was SAML (Security Assertion Markup Language)...

Eva Vetter
Jul 3, 20251 min read

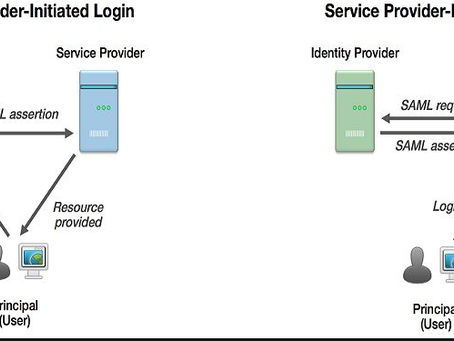
SAML SSO 101
I have been asked countless times by my professional network why I am so intrigued with SSO (Single Sign On) technologies. The answer is...

Eva Vetter
Jul 3, 20252 min read


A Love Letter to IAM (Identity Access Management)
A love letter to IAM (Identity Access Management): I recall the initial skepticism when I shared my fascination with all things Identity....

Eva Vetter
Jul 3, 20251 min read
bottom of page